Recent searches
Search options
#perl
An approach for process injection (in #linux) with #Perl.
https://isra.cl/articles/furia.html
Paired with the definitive guide to linux #injection
https://www.akamai.com/blog/security-research/the-definitive-guide-to-linux-process-injection
I can't really figure this one out, please help.
I have a whole bunch of modules that layer on each other and I decided to try to use Mojo::Promise to go async. After running into issues I tried to mock some code on the command line and both M:P and Future do the same in that the inner "then"s do not seem to do anything.
```
sub outer{my $p=inner()->then(sub{say "o"}); $p}
sub inner{my $p=Mojo::Promise->new->then(sub{say "i"});$p->timer(1); $p}
outer->wait();
```
prints o only.
Shocking news!
“perl -c script.py” will give you tons of errors!
Apparently it's getting to be too late to get any complex programming done tonight, then.
After a few months of research I'm publishing a new article on my weblog. It's called "Furia: an approach for process injection with Perl". It discusses a Perl implementation of the ROP stack hijacking technique using the process_vm_writev syscall. Link: https://isra.cl/articles/furia.html #perl #linux
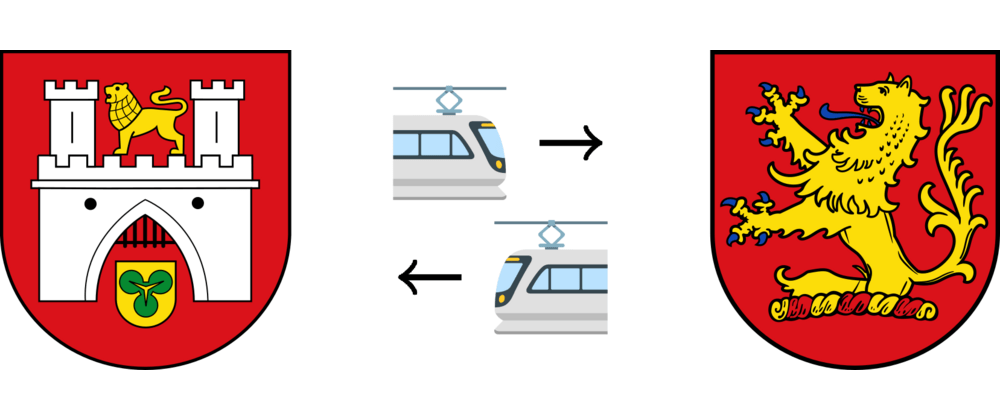
@manwar 's post in last year’s #Perl Advent Calendar about his Map::Tube module intrigued me. I decided I wanted to build a map for the tram network where I live: Hannover. Along the way, I decided to write up how to create a Map::Tube map for one’s city of interest. Since I enjoy explaining things in detail, this got … long. So I broke it up into parts.
This is the first post in a five-part series about how to create Map::Tube maps. Enjoy!
https://peateasea.de/building-map-tube-whatever-maps-a-howto-first-steps/
About 25 years ago, I disliked that so many Debian tools were written in Perl because the language allowed too many ways to do the same thing. Now, I consider Perl 5 mature and predictable compared to Python 3.
A favorite hobby of mine has become collecting outdated, preferably chintzy, tech books. My most recent is the MS-DOS 6.2 guide.
#Perl @PerlWChallenge 317 Acronyms and Friendly Strings https://wlmb.github.io/2025/04/14/PWC317/
#noxp
Alerte sécurité #Perl – CVE-2024-56406
Si vous avez une solution ou un site exposé sur Internet avec Perl (v5.34 à v5.40), prenez 1 min pour lire ceci
Une faille heap buffer overflow dans l’opérateur tr/// permet de planter Perl via une simple ligne de code :
perl -e '$_ = "\x{FF}" x 1000000; tr/\xFF/\x{100}/;'
Risque d'attaque opportuniste par déni de service
Possiblement à risque si exposés:
Portails d'hébergements mutualisés
Scripts Perl manipulant des entrées utilisateur
Stacks locales (ex : XAMPP)
Pour se protéger :
Mettez à jour en 5.40.2 ( https://metacpan.org/release/SHAY/perl-5.40.2/changes) ou 5.38.4 (https://metacpan.org/release/SHAY/perl-5.38.4/changes)
cPanel
https://docs.cpanel.net/changelogs/110-change-log/#110058

The Weekly Challenge - 317 #Perl #RakuLang
Task 1: Acronyms
Task 2: Friendly Strings
https://theweeklychallenge.org/blog/perl-weekly-challenge-317

Here is an upbeat tune I made:
https://geneboggs.bandcamp.com/track/parabola
I used the #Perl program https://metacpan.org/release/GENE/MIDI-RtController-Filter-CC-0.0603/source/eg/multi.pl to help create it. Specifically, it makes the bass sound like a farty didgeridoo and the arpeggiation more vibrant. :D
You can soon download both from your favorite #CPAN mirror or find them at:
https://metacpan.org/release/SHAY/perl-5.40.2/
https://metacpan.org/release/SHAY/perl-5.38.4/
Changes are listed in their respective “perldelta” documents:
https://metacpan.org/release/SHAY/perl-5.40.2/view/pod/perldelta.pod
https://metacpan.org/release/SHAY/perl-5.38.4/view/pod/perldelta.pod

The Weekly Challenge 316: Circular Reasoning #Perl #RakuLang #RustLang #Postscript #CrystalLang #PerlWeeklyChallenge #BlogFiredrakeOrg https://blog.firedrake.org/archive/2025/04/The_Weekly_Challenge_316__Circular_Reasoning.html
@brainblasted agree with Rust, #Perl & Python
are equal in quality & older.
I do wish #Rust had the #Python tutorial.
Up to date and covers the basics with the latest version. This point is so important, have correct usable documentation at each release. No half completed information allowed. <https://docs.python.org/3/tutorial/index.html>

#Perl is actively maintained with regular releases.



 decio
decio